Virtual port channel (vPC) typically used for providing active-active connection from switch to end-point devices. However, due to it provide loop free design, we can configure one vPC domain on aggregation switches to other vPC domain on access switches while it providing more bandwidth for access switches to aggregation switches. This type of vPC called Double-Sided vPC or back-to-back vPC.
In this lesson, we will learn to configure Double-Sided vPC (back-to-back vPC). Before going into deep, if you need help on basic vPC configuration you can check out How to configure Cisco Nexus vPC. Now, let’s get started.
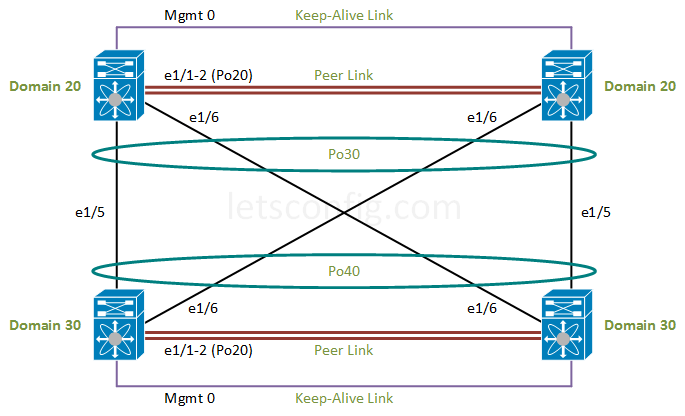
Enabling Features:
First of all, let’s enable lacp and vpc features on all four nexus switches.
feature vpc feature lacp
Keep-Alive Link
For keep-alive link, we are using management interfaces for all four switches. You can choose other interfaces as well. Point-to-point IP is 10.1.1.0/30 for N7K-01 and N7K-02.
N7K-01 Switch: N7K-01(config)# interface mgmt 0 N7K-01(config-if)# description ***vPC Keep-Alive Link*** N7K-01(config-if)# ip address 10.1.1.1/30 N7K-01(config-if)# no shutdown N7K-02 Switch: N7K-02(config)# interface mgmt 0 N7K-02(config-if)# description ***vPC Keep-Alive Link*** N7K-02(config-if)# ip address 10.1.1.2/30 N7K-02(config-if)# no shutdown
Let’s verify the reachability from 10.1.1.1 to 10.1.1.2 IP.
N7K-01# ping 10.1.1.2 vrf management PING 10.1.1.2 (10.1.1.2): 56 data bytes 64 bytes from 10.1.1.2: icmp_seq=1 ttl=254 time=0.688 ms 64 bytes from 10.1.1.2: icmp_seq=2 ttl=254 time=0.698 ms 64 bytes from 10.1.1.2: icmp_seq=3 ttl=254 time=0.568 ms 64 bytes from 10.1.1.2: icmp_seq=4 ttl=254 time=0.566 ms 64 bytes from 10.1.1.2: icmp_seq=5 ttl=254 time=0.583 ms --- 10.1.1.2 ping statistics --- 5 packets transmitted, 5 packets received, 0.00% packet loss round-trip min/avg/max = 0.566/0.698/0.6206 ms
For other peer of Nexus switches (N7K-03 and N7K-04), we are using 10.2.2.0/30 as keep-alive point-to-point IP.
N7K-03 Switch: N7K-03(config)# interface mgmt 0 N7K-03(config-if)# description ***vPC Keep-Alive Link*** N7K-03(config-if)# ip address 10.2.2.1/30 N7K-03(config-if)# no shutdown N7K-04 Switch: N7K-04(config)# interface mgmt 0 N7K-04(config-if)# description ***vPC Keep-Alive Link*** N7K-04(config-if)# ip address 10.2.2.2/30 N7K-04(config-if)# no shutdown
Let’s verify the reachability from 10.2.2.1 to 10.2.2.2 IP.
N7K-03# ping 10.2.2.2 vrf management PING 10.2.2.2 (10.2.2.2): 56 data bytes 36 bytes from 10.2.2.2: Destination Host Unreachable Request 0 timed out 64 bytes from 10.2.2.2: icmp_seq=1 ttl=254 time=1.098 ms 64 bytes from 10.2.2.2: icmp_seq=2 ttl=254 time=0.598 ms 64 bytes from 10.2.2.2: icmp_seq=3 ttl=254 time=0.536 ms 64 bytes from 10.2.2.2: icmp_seq=4 ttl=254 time=0.503 ms --- 10.2.2.2 ping statistics --- 5 packets transmitted, 4 packets received, 20.00% packet loss round-trip min/avg/max = 0.503/0.683/1.098 ms
vPC Domain:
For first peer of vPC, below are the domain configuration. We are making N7K-01 as primary and N7K-02 is secondary.
N7K-01(config)# vpc domain 20 N7K-01(config-vpc-domain)# role priority 100 N7K-01(config-vpc-domain)# peer-keepalive destination 10.1.1.2 source 10.1.1.1 vrf management N7K-02(config)# vpc domain 20 N7K-02(config-vpc-domain)# role priority 200 N7K-02(config-vpc-domain)# peer-keepalive destination 10.1.1.1 source 10.1.1.2 vrf management
For second peer of vPC, we are choosing N7K-03 as primary and N7K-04 as secondary. Here note that, vPC domain id needed to be unique, which means you can not use this id anywhere else in your network.
N7K-03(config)# vpc domain 30 N7K-03(config-vpc-domain)# role priority 100 N7K-03(config-vpc-domain)# peer-keepalive destination 10.2.2.2 source 10.2.2.1 vrf management N7K-04(config)# vpc domain 30 N7K-04(config-vpc-domain)# role priority 200 N7K-04(config-vpc-domain)# peer-keepalive destination 10.2.2.1 source 10.2.2.2 vrf management
Peer Link Configuration
For vPC peer-link, we are using same interfaces for simplicity in this example. So, configuration will be same for both switches.
N7K-01 to N7K-04: interface ethernet 1/1-2 no shutdown description ***vPC PEER-LINK*** channel-group 20 mode active interface port-channel 20 no shutdown description ***vPC PEER-LINK*** switchport switchport mode trunk switchport trunk allowed vlan all vpc peer-link
In the next step, we need to configure member port for each vPC.
Member port Configuration
For vPC peer 1, we need to add below configuration.
interface ethernet 1/5-6 no shutdown description ***vPC Member Port*** channel-group 30 mode active interface port-channel 30 no shutdown switchport switchport mode trunk switchport trunk allowed vlan add all vpc 30
For vPC peer 2, we need to add below configuration.
interface ethernet 1/5-6 no shutdown description ***vPC Member Port*** channel-group 40 mode active interface port-channel 40 no shutdown switchport switchport mode trunk switchport trunk allowed vlan add all vpc 40
Verification:
Use “show vpc brief” command to check the VPC status.
N7K-01# show vpc brief
Legend:
(*) - local vPC is down, forwarding via vPC peer-link
vPC domain id : 20
Peer status : peer adjacency formed ok
vPC keep-alive status : peer is alive
<-- Output Omitted --> For more information, you can check Cisco reference guide for vPC.


As per the design both the switches will act as single switch logically
so logically we willl be having two nexus switches and two lacp bundle will be formed between them , so now does stp block one lacp bundle
It’s a single port-channel. No chance for loop here.
What about STP? Do we need to implement STP here?
No need..
Hi Rajib,
How to use the same design on to sites as OLALEKAN SOBANKE wrote in the first comment. I want to migrate one site to another with minimum downtime and keep the IP-address.
Does it work in this way:
Site A domain 20
Site B domain 30
Site A and B use domain 40
Then trunk and across VLAN.
OR I have to use Multilayer vPC?
Hi Rajib,
In your configuration example picture and the configuration, you have two different port-channels configured (po30 & po40) for the links between all 4 Nexus switches. Am I correct in assuming that only one port-channel would also work? Or would two have to be used? (N7K-1N7K-3 = po30; N7K-2N7K-4 = po40)?
Thank you for your time!
Hi Josh,
In this scenario, i used two different port-channel id for top two amd bottom two swtithes. Both port-channel have to be functional. Po30 is for top two switches & Po40 for bottom two switches.
vpc id should be the same on all member ports
Hi, Rajib,
great guides by the way, always nice to see people sharing there expertise!
Would I be able to link the sets of VPC Peers via 1 uplink from each switch instead of the 2 in the guide.
I currently on have 2 fibre pairs between my data centres, so I’m thinking to create a link use the 2 pairs then have 2 more pairs installed soon.
Let me know your thoughts and any disadvantages with my setup.
Thanks
Yes, you can do that. There is no issue on that design.
Hi Rajib,
Will linking the two VPC’s via two interfaces instead of four work temporarily?
I.E. one Fibre link from each peer to the other side?
I would like to setup the doubles sides VPC before our second fibre cables are installed.
What are the disadvantages if it is viable?
Go for it. There is no issue.
Hi Rajib , will this confguration work on n3k-c3064 ?
Yes, it should work.
Hi Rajib! Thank for all your precious tutorials. If i need to add 2 switches more on the same “level” of Domain30, do i need to create a new domain (Eg. Domain31) and new port channel on “main” switches (Eg. Po31)? (Then I will follow similar config for N7K-03 and N7K-04).
I aplogogize if I’m not too clear, I can send you a diagram to better understand if you think so. Thank you!
Share me your diagram.
Hi
in this scenario can I create single port-channel between 4 nexus switch
It’s already single port-channel.
Dear As per the design picture interfaces are eth1/5-6 and configuration eth2/5-6 ? am new to nexus need help to avoid misunderstanding.
Hi Arahman, you are right. I forgot to update interfaces in the diagram. As a quick fix, i made interface 2/5-6 to 1/5-6 in configuration.
If you want to learn more about nexus, you can check https://www.letsconfig.com/category/cisco/switching-cisco/nexus/ and subscribe by blog.
You are the Best brother fantastic, i actually have this setup but with extended 8 additional 5k in my two DR sites extending the VLANs across the WAN with fabric path such cool solutions for me to migrate my servers with the same ip from one location to another. The domain aspect is very important to me and i am keenly learning and reading more.
Thanks so much for sharing, May God bless you
You are most welcome 🙂