When we need a secure connection between multiple fixed location, site-to-site VPN is one of the most popular option for network engineers. Today, in this lesson, we will learn how to configure site-to-site policy based IPSec VPN on juniper SRX firewall.
We will be using below diagram for our IPSec lab. We assume that, CTG end configuration is already completed. Here we will configure our DHK end firewall only.
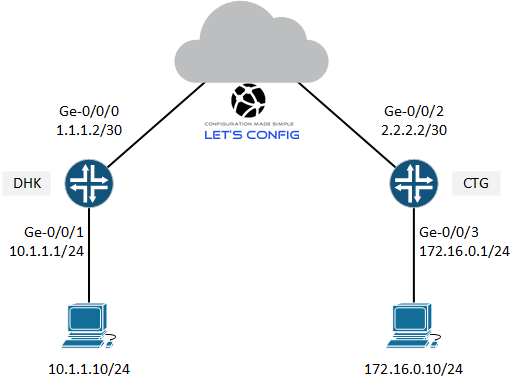
VPN Gateway Details:
| VPN IP Details | DHK | CTG |
| VPN Gateway IP | 1.1.1.2 | 2.2.2.2 |
| LAN IP | 10.1.1.0/24 | 172.16.0.0/24 |
VPN NegotiationParameters:
| Phase 1 | |
| Authentication Method | Pre-Shared Key |
| Authentication-algorithm | sha-256 |
| Diffie-Hellman Group | Group 5 |
| Encryption Algorithm | 3des-cbc |
| Lifetime (for renegotiation SEC) | 86400 |
| Main or Aggressive Mode | Main |
| Pre Shared Key | letsconfig |
| Phase 2 | |
| Encapsulation (ESP or AH) | ESP |
| Encryption Algorithm | 3des-cbc |
| Authentication Algorithm | hmac-sha1-96 |
| Perfect Forward Secrecy | No PFS |
| Lifetime (for renegotiation) | 28800 |
Configuration:
First of all, let’s verify the ping reachability from DHK end to CTG end IP.
root@DHK> ping 2.2.2.2 PING 2.2.2.2 (2.2.2.2): 56 data bytes 64 bytes from 2.2.2.2: icmp_seq=0 ttl=63 time=11.684 ms 64 bytes from 2.2.2.2: icmp_seq=1 ttl=63 time=10.274 ms 64 bytes from 2.2.2.2: icmp_seq=2 ttl=63 time=10.190 ms 64 bytes from 2.2.2.2: icmp_seq=3 ttl=63 time=10.640 ms ^C --- 2.2.2.2 ping statistics --- 4 packets transmitted, 4 packets received, 0% packet loss round-trip min/avg/max/stddev = 10.190/10.697/11.684/0.594 ms root@DHK>
Ping result shows a full reachability to ipsec peer IP.
We also need to check IKE is allowed in our untrust (outside) zone or not. If it’s not allowed we have to allow it.
root@DHK# show | display set | match security-zone set security zones security-zone untrust host-inbound-traffic system-services all set security zones security-zone untrust host-inbound-traffic protocols all set security zones security-zone untrust interfaces ge-0/0/0.0
Here, in our lab everything is allowed. You might need to allow specific services in production networks. If you do so, make sure Ike is allowed which is must needed to form IPSec peer. Use below command to allow.
set security zones security-zone untrust host-inbound-traffic system-services ike
Now, move to the main part of ipsec configuration. Here we will configure Phase 1 and 2.
IKE_Proposal: We will configure IKE proposal, according our ipsec parameter table.
set security ike proposal our-ike-proposal authentication-method pre-shared-keys set security ike proposal our-ike-proposal dh-group group5 set security ike proposal our-ike-proposal authentication-algorithm sha-256 set security ike proposal our-ike-proposal encryption-algorithm 3des-cbc set security ike proposal our-ike-proposal lifetime-seconds 86400
IKE_Policy: Our pre-shared-key is “letsconfig” which will be added here and combine proposal here with it.
set security ike policy our-ike-policy mode main set security ike policy our-ike-policy proposals our-ike-proposal set security ike policy our-ike-policy pre-shared-key ascii-text letsconfig
IKE_Gateway: Here we will assign our external interface, peer id, and ike policy.
set security ike gateway our-ike-gateway ike-policy our-ike-policy set security ike gateway our-ike-gateway address 2.2.2.2 set security ike gateway our-ike-gateway external-interface ge-0/0/0.0
Now move to the phase 2 configuration.
IPSec_Proposal: IPsec proposal parameter are given above.
set security ipsec proposal our-ipsec-proposal protocol esp set security ipsec proposal our-ipsec-proposal authentication-algorithm hmac-sha1-96 set security ipsec proposal our-ipsec-proposal encryption-algorithm 3des-cbc set security ipsec proposal our-ipsec-proposal lifetime-seconds 28800
IPSec_Policy: In IPsec policy section, we will announce our IPSec proposal into the policy.
set security ipsec policy our-ipsec-policy proposals our-ipsec-proposal
IPSec_VPN: This is the section where phase 1 and phase 2 join together.
set security ipsec vpn our-ipsec-vpn-1 ike gateway our-ike-gateway set security ipsec vpn our-ipsec-vpn-1 ike ipsec-policy our-ipsec-policy set security ipsec vpn our-ipsec-vpn-1 establish-tunnels immediately
Let’s define our inside and outside IP addresses just like below.
set security zones security-zone untrust address-book address out-ip 172.16.0.0/24 set security zones security-zone trust address-book address in-ip 10.1.1.0/24
Now, We need to configure security policy for our policy based IPSec VPN.
Inside to Outside policy:
edit security policies from-zone trust to-zone untrust policy in-to-out
set match source-address in-ip
set match destination-address out-ip
set match application any
set then permit tunnel ipsec-vpn our-ipsec-vpn-1
set then permit tunnel pair-policy out-to-in
Outside to inside policy:
edit security policies from-zone untrust to-zone trust policy out-to-in
set match source-address out-ip
set match destination-address in-ip
set match application any
set then permit tunnel ipsec-vpn our-ipsec-vpn-1
set then permit tunnel pair-policy in-to-outVerification:
The first command will show our phase 1 status and second one will show phase 2 status.
- run show security ike security-associations
- run show security ipsec security-associations
root@DHK# run show security ike security-associations Index State Initiator cookie Responder cookie Mode Remote Address 3042402 UP e0537e4ce947e7f6 1c1ce74c43f4c092 Main 2.2.2.2
Output shows our phase 1 is UP. Now, lets check pahse 2 status.
root@DHK# run show security ipsec security-associations Total active tunnels: 1 ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway <2 ESP:3des/sha1 2ad8a287 17791/unlim - root 500 2.2.2.2 >2 ESP:3des/sha1 c6671bf7 17791/unlim - root 500 2.2.2.2
It’s confgirmed that our tunnel are up.
“run show security ipsec statistics” is another useful command which shows the encryption and decryption count.
root@DHK# run show security ipsec statistics ESP Statistics: Encrypted bytes: 1296304 Decrypted bytes: 834828 Encrypted packets: 9532 Decrypted packets: 9947 AH Statistics: Input bytes: 0 Output bytes: 0 Input packets: 0 Output packets: 0 Errors: AH authentication failures: 0, Replay errors: 0 ESP authentication failures: 0, ESP decryption failures: 0 Bad headers: 0, Bad trailers: 0 [edit] root@DHK#
Now, ping from 10.1.1.10 PC to 172.16.0.10.
C:\>ping 172.16.0.10
Pinging 172.16.0.10 with 32 bytes of data:
Reply from 172.16.0.10: bytes=32 time=5ms TTL=115
Reply from 172.16.0.10: bytes=32 time=4ms TTL=115
Reply from 172.16.0.10: bytes=32 time=6ms TTL=115
Reply from 172.16.0.10: bytes=32 time=5ms TTL=115
Ping statistics for 172.16.0.10:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 4ms, Maximum = 6ms, Average = 5ms
C:\>So, it’s working 🙂
Juniper provides a fantastic tool to generate Site-to-Site VPN Configuration for SRX & J Series devices. Please have a look – https://www.juniper.net/support/tools/vpnconfig/


Hi,
Thanks that seemed to have worked.. I can now see phase 1 is up but phase 2 is failing due to ‘Phase2 finish: No sa_cfg found!’.
> show security ike security-associauions
Index Remote Address State Initiator cookie Responder cookie Mode
1686440 192.168.0.64 UP 0cb7c8787379f19f a5262ced56b54627 Main
But thank you for all your help ill carry out some further checks on that.
Hi thnnks for the response..
Im afraid still persists:
[edit security policies from-zone trust to-zone untrust policy in-to-out]
# set match application any
[edit security policies from-zone trust to-zone untrust policy in-to-out]
# commit check
[edit security policies from-zone untrust to-zone trust policy out-to-in]
‘match’
Missing mandatory statement: ‘application’
#show
match {
source-address in-ip;
destination-address out-ip;
##
## Warning: application or application-set must be defined
##
application [ any then ];
}
then {
permit {
Thanks
There is no application named “then”. So, run below command and check, it will work.
“delete application then”
Hi thanks.,.. this is great.. I have 2 srx’s 210 and 110.. on the 210 however getting this error :
[edit security policies from-zone trust to-zone untrust policy in-to-out]
‘match’
Missing mandatory statement: ‘application
Ive added the then permit statement but to no avail.. any ideaas.. sorry im new to juniper so might be an easy change.
thanks again for this..
” Missing mandatory statement: ‘application’ ”
So, you need to include the application. Add below command and share outcome.
edit security policies from-zone trust to-zone untrust policy in-to-out
set match application any
Thanks. And how I’m glad 🙂
🙂 Thank you for reaction.
Now the problem is solved. But… there is my mistake: version with a problem is 10.3R4.5. With 12.1 was better.
For 10.3… I don’t now what and how…. 🙂 at the end I’d done “deactivate security ike” and “… ipsec” and then “activate… ” both of them… And the ping inside the tunnel lifted up.
The “generator” (from the Juniper site) hadn’t solved the problem before 🙂
I’m sure there are some moments beside configuration: sequence of steps.
Thanks again.
And – yes: a particelar version and SRX240B
Hi maccim, glad to know your problem is solved.
Dec 5 09:22:47 kmd[1164]: KMD_VPN_UP_ALARM_USER: VPN OUR-VPN from 1.1.1.2 is up. Local-ip: 2.2.2.2, gateway name: OUR-IKE-GATEWAY, vpn name: OUR-VPN, tunnel-id: 131073, local tunnel-if: st0.0, remote tunnel-ip: 192.168.0.1, Local IKE-ID: 2.2.2.2, Remote IKE-ID: 1.1.1.2, XAUTH username: Not-Applicable, VR id: 0, Traffic-selector: , Traffic-selector local ID: ipv4_subnet(any:0,[0..7]=0.0.0.0/0), Traffic-selector remote ID: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Dec 5 09:26:00 kmd[1164]: KMD_DPD_PEER_DOWN: DPD detected peer 1.1.1.2 is dead, so dropping the tunnel
Dec 5 09:26:00 kmd[1164]: KMD_VPN_DOWN_ALARM_USER: VPN OUR-VPN from 1.1.1.2 is down. Local-ip: 2.2.2.2, gateway name: OUR-IKE-GATEWAY, vpn name: OUR-VPN, tunnel-id: 131073, local tunnel-if: st0.0, remote tunnel-ip: 192.168.0.1, Local IKE-ID: 2.2.2.2, Remote IKE-ID: 1.1.1.2, XAUTH username: Not-Applicable, VR id: 0, Traffic-selector: , Traffic-selector local ID: ipv4_subnet(any:0,[0..7]=0.0.0.0/0), Traffic-selector re
What is your JunOS version. Did you configured DPD? Can you ping vpn peer IP?
Well, I have a question… Maybe you have any comment 🙂
I try to make some ipsec tunnels. It’s possible without problems if JunOS 12.1X44-D60.2. Three routers of my small lab make tunnels. Other versions – troubles.
There is a situation for two routers:
1.
12.1X44-D60.2 name – KAB
result of >show log kmd-log
Mar 22 09:38:36 Group/Shared IKE ID VPN configured: 0
Mar 22 10:07:49 Group/Shared IKE ID VPN configured: 0
Mar 22 10:08:48 Group/Shared IKE ID VPN configured: 0
Mar 22 10:11:26 Group/Shared IKE ID VPN configured: 0
Mar 22 10:11:45 Group/Shared IKE ID VPN configured: 0
Mar 22 10:15:14 Group/Shared IKE ID VPN configured: 0
root@kab# run show security ipsec security-associations
Total active tunnels: 1
ID Algorithm SPI Life:sec/kb Mon vsys Port Gateway
131073 ESP:3des/sha1 14dad711 3584/ unlim – root 500 172.20.7.226
2.
12.1X44-D60.2 name – FON
Mar 22 11:47:55 Group/Shared IKE ID VPN configured: 0
Mar 22 12:07:53 Group/Shared IKE ID VPN configured: 0
Mar 22 12:08:46 Group/Shared IKE ID VPN configured: 0
Mar 22 12:11:22 Group/Shared IKE ID VPN configured: 0
Mar 22 12:11:42 Group/Shared IKE ID VPN configured: 0
Mar 22 12:15:19 Group/Shared IKE ID VPN configured: 0
admin@FON# run show security ipsec security-associations
Total active tunnels: 1
ID Algorithm SPI Life:sec/kb Mon vsys Port Gateway
131073 ESP:3des/sha1 ddf604eb 3578/ unlim – root 500 172.20.15.194
If I try to make a tunnel to a router with the other version JunOS – I have the same result: ike and ipsec phases done successfulle, but there are not even ping from one tunnel end to other.
The advised vpn generator – gives the same result.
To update JunOS – maybe a problem. One point is too far.
Thank you.
Are you facing problem for a particular version? What hardware you are using?
Thank you for the post
but its seems to have issue on my end ,the VPN keep going down and can’t ping from VPC to VPC
You can share your configuration. I will check and give you feedback accordingly.