High availability (HA) is a type of deployment, where 2 firewalls are positioned in a group and their configuration is synchronized to avoid a single point of failure in a network. In this lesson, we will learn to configure Active/Passive HA in Palo Alto Firewall.
Prerequisite:
- Same firewall model with same PAN-OS version.
- Same version of App, Threat, Antivirus, GlobalProtect in both firewall.
- Check all licenses are identical.
You can read more details about all prerequisites from PaloAlto administrative guide.
LAB Diagram:
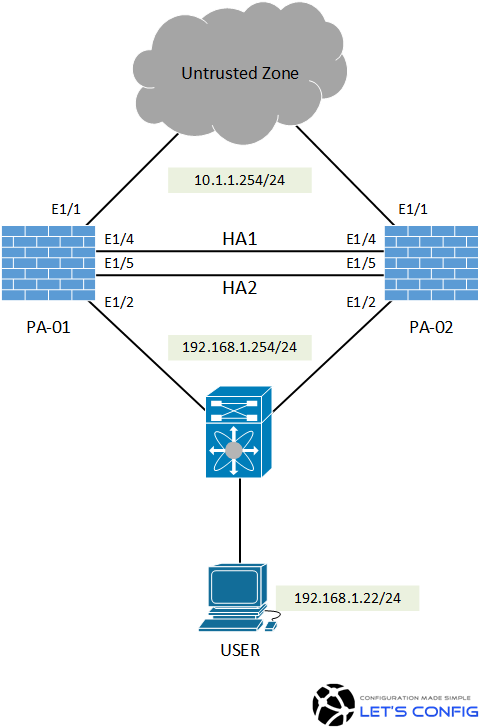
Active/Passive HA Configuration in Palo Alto Firewall:
HA Ports:
We do not have any dedicated HA1 and HA2 ports. So, we are going to make ethernet1/4 as HA1 and ethernet1/5 as HA2. To do this, we need to go – Network >> Interface >> Ethernet. And, then need to change the interface type for ethernet1/4 and ethernet1/5 as HA port just like below.
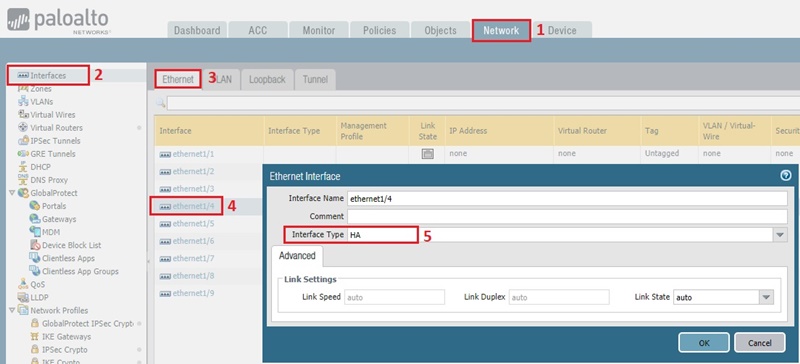
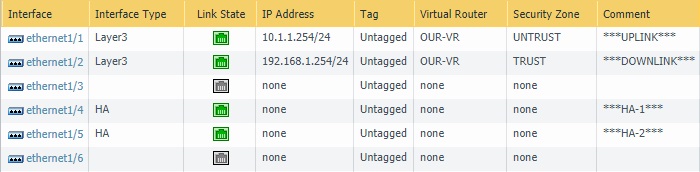
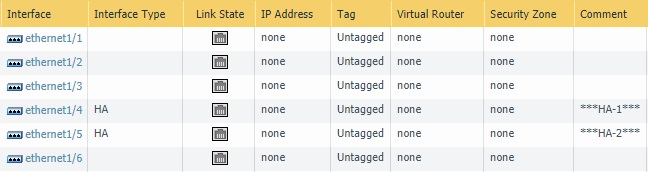
The final output will look like below-
PA-01:
PA-02:
Control Plane Configuration
In the next section, we need to go Device >> High Availability. Now, by clicking on top right gear icon in Control Link (HA1) section, we will declare ethernet1/4 as our control plane link (HA1) as we decided earlier.
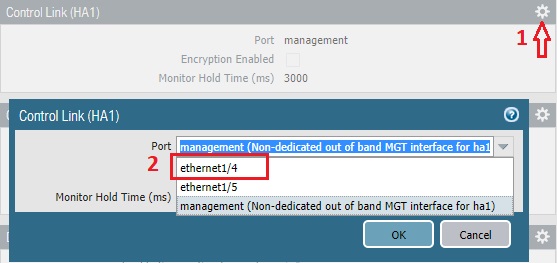
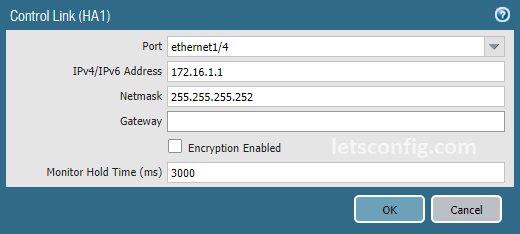
We will be using 172.16.1.0/30 for HA1 link. Below are the configuration of Active and Passive nodes. It’s Point-to-Point, so we do not need any gateway here.
PA-01:
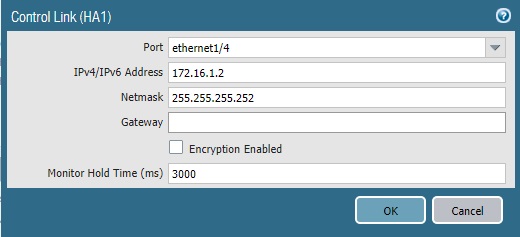
PA-02:
Data Link Configuration:
On the same page (Device >> High Availability), we need to click on top right gear icon in Data Link (HA2) section.
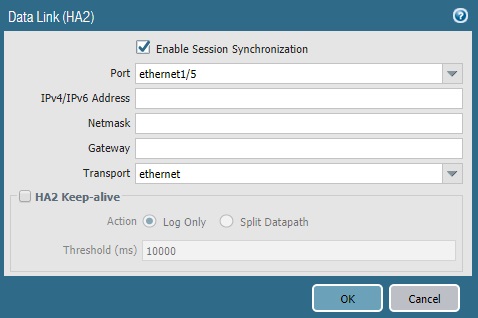
In our case, ethernet1/5 is our HA2 link. It’s directly connected, so transport mode is ethernet. We do not need to specify any IP address. However, if your data link is coming through L3 networks, then you need to specify IP details.
Group Configuration:
In the next section, we will enable HA, add Group ID and put Peer HA1 IP Address. Below are the configuration of PA-01 firewall.
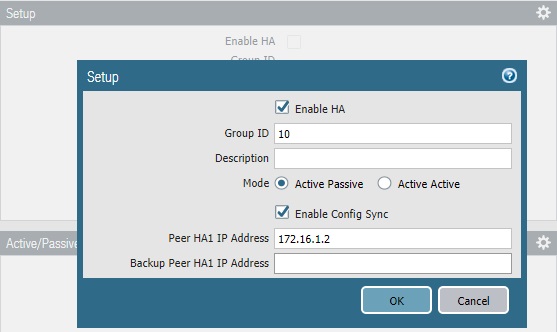
Similarly, we need to enable HA on PA-02. Provide same group ID (10) and add Peer HA1 IP as 172.16.1.1.
Priority and Preemption:
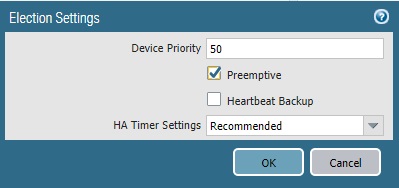
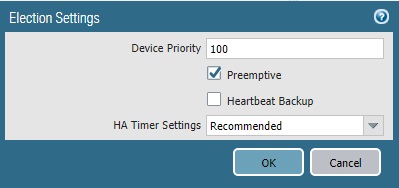
This section is optional but recommended. Here we will add device priority to prefer PA-01 as Active unit. And also, preemption will be enabled to make sure whenever PA-01 firewall is up and running, it handles the traffic. The firewall with the lower value will be Active and the other firewall is the Passive firewall.
Note: If you didn’t change device priority, then the lowest MAC address on HA1 link will act as Active firewall.
PA-01:
PA-02:
Verify:
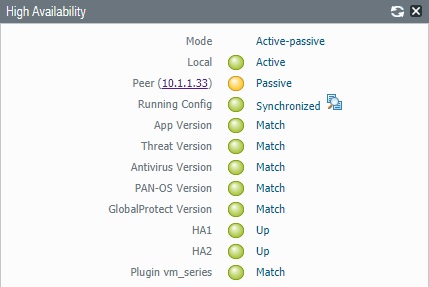
There is an easy way to verify the HA status. Just go to Dashboard >> Widgets >> System >> High Availability.
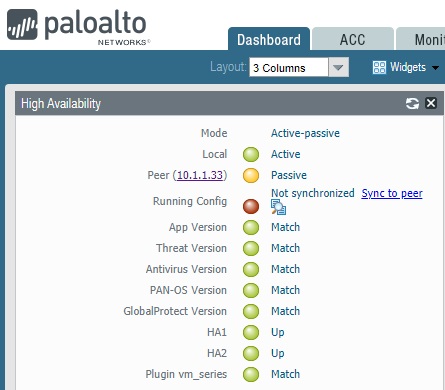
You can see our Active-Passive HA is already formed. However, configuration doesn’t sync yet. We can follow below to sync configuration from Active to Passive unit.
Option 1:
We can just click on “Sync to peer”. It will automatically sync configuration from Active unit to Passive unit.
Option 2:
We can run below command-
admin@PA-ACTIVE(active)> request high-availability sync-to-remote running-config Executing this command will overwrite the candidate configuration on the peer and trigger a commit on the peer. Do you want to continue(y/n)? (y or n) y HA synchronization job has been queued on peer. Please check job status on peer. admin@PA-ACTIVE(active)>
Here is the final output of HA widget.


Hi Rajib,
With this setup we can access the passive Unit of the HA pair locally. Do you know if there is a way we can access the passive unit remotely?
Thanks,
Mike
Your management IP need to be routed in internet or you have to use VPN to access your passive unit.
Can we access both the firewall.
At the time of sync is managment IP is also synced?
Management IPs have to be different. And, they will not be synced.
Thanks for your help
Switch configuration (connected ports) need to be L2. You can configure IP on interface-vlan or you can configure it on your router end.
ok. but are they supposed to be a total of 3 ips, or at least a VIP ?
I am seeing only 192.168.1.254.
Two IPs, one for PaloAlto and one for VIP (gateway).
whats the configuration at the 2x Switch Ports ? Do I need to put a IP on each of the switch interface ?
hello sir i configured HA, everything is working perfect, but after suspending my PA1 it’s wait till 300 sec to forward traffic from PA2, means it’s waiting till mac-table aging time.
Go to Network >> High Availability >> General >> Election Settings and change HA timer setting to Aggressive. It will be much quicker.
Thanks for the response.
Sorry, I should have been more clearer. On the last picture the peer (passive) IP is showing as 10.1.1.33. I presume we can use that IP to log in to the passive unit. I was wondering how can we use an UNTRUST IP to access the passive peer. My understanding is that we can only use the Management IP to connect to the passive node.
10.1.1.33 is the management IP for passive unit. After configuring management IP, you only need to configure HA1 and HA2 link. All other configuration will be sync automatically.
Nice article. Out of interest, how did you configure the peer IP of 10.1.1.33 on the passive PA?
Hi Suresh, i can’t find the section where i configured 10.1.1.33.
However, you only need to configure HA1 and HA2 in the Passive unit, other confirmation will be auto sync.